Top 10 Smart Contract Vulnerabilities and How to Audit Them Before Deployment
In the fast-moving world of Web3, smart contract vulnerabilities remain a leading cause of financial loss. From reentrancy bugs to logic flaws, attackers continuously exploit weak points in decentralized applications (dApps). A thorough smart contract audit checklist is no longer optional—it’s the backbone of blockchain security.This article explores the top 10 vulnerabilities that developers and auditors must understand, along with practical ways to detect and mitigate them before deployment.
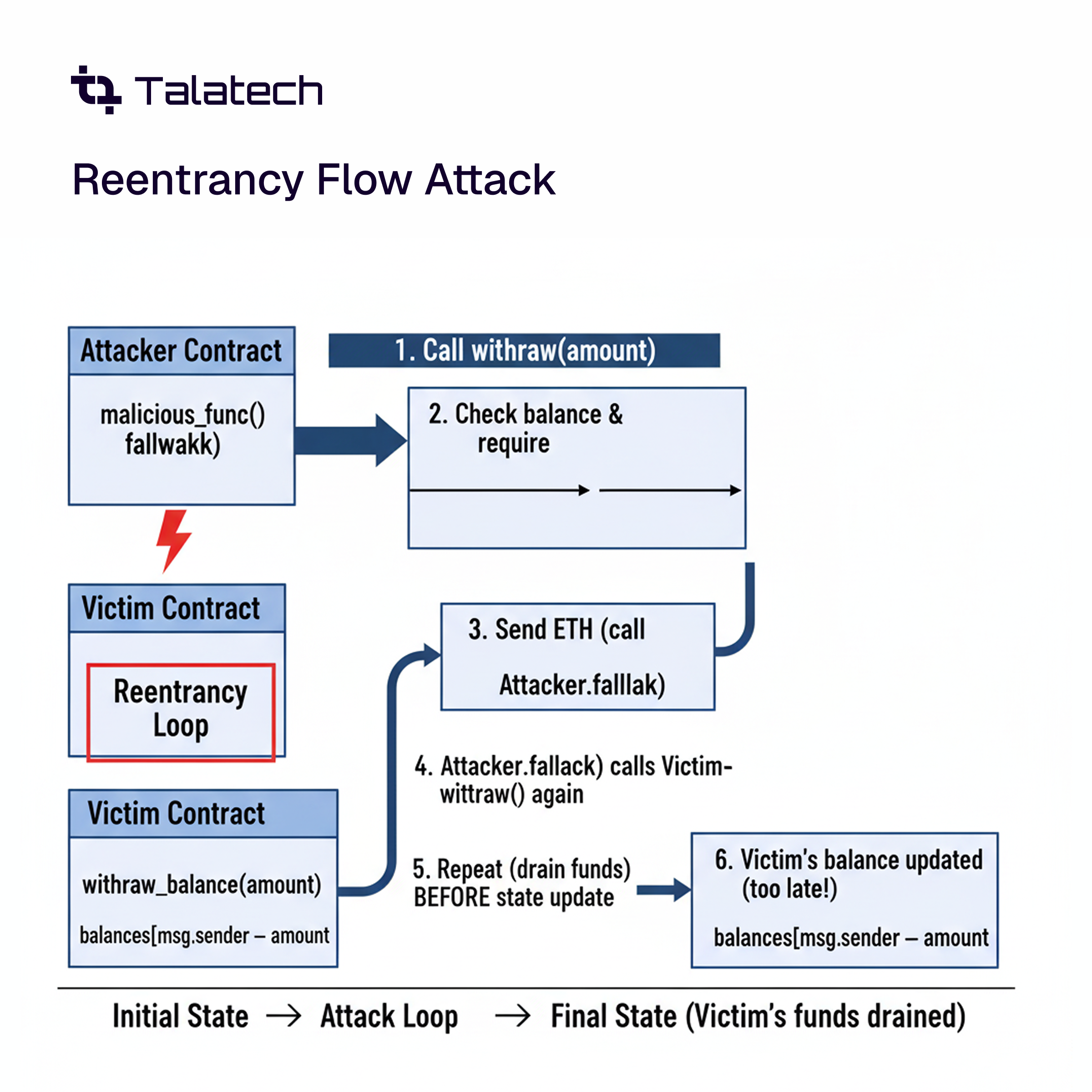
1. Reentrancy Attacks
What it is
A reentrancy attack occurs when a contract calls an external contract before updating its internal state, allowing attackers to repeatedly withdraw funds.
Example: The infamous DAO hack exploited this flaw, draining millions in ETH.
How to Audit:
- Ensure state updates occur before external calls.
- Use the checks-effects-interactions pattern.
- Implement reentrancy guards (nonReentrant modifier in OpenZeppelin).
2. Integer Overflow and Underflow
What it is:
Mathematical operations can exceed variable limits, causing logic errors or financial manipulation.
How to Audit:
- Use SafeMath or Solidity 0.8+ built-in checks.
- Add unit tests for boundary values.
- Perform fuzz testing for arithmetic vulnerabilities.
3. Unchecked External Calls
What it is:
External contract calls can fail silently if not handled properly, leading to incomplete transactions or inconsistencies.
How to Audit:
- Use require(success) after call() or send().
- Prefer OpenZeppelin’s Address library for secure calls.
- Trace all call hierarchies during the audit.
4. Access Control Misconfiguration
What it is:
Improperly set admin privileges can allow anyone to perform restricted actions like minting or pausing tokens.
How to Audit:
- Review modifier logic for access functions.
- Check for hardcoded owner addresses.
- Implement multi-signature authorization for critical functions.
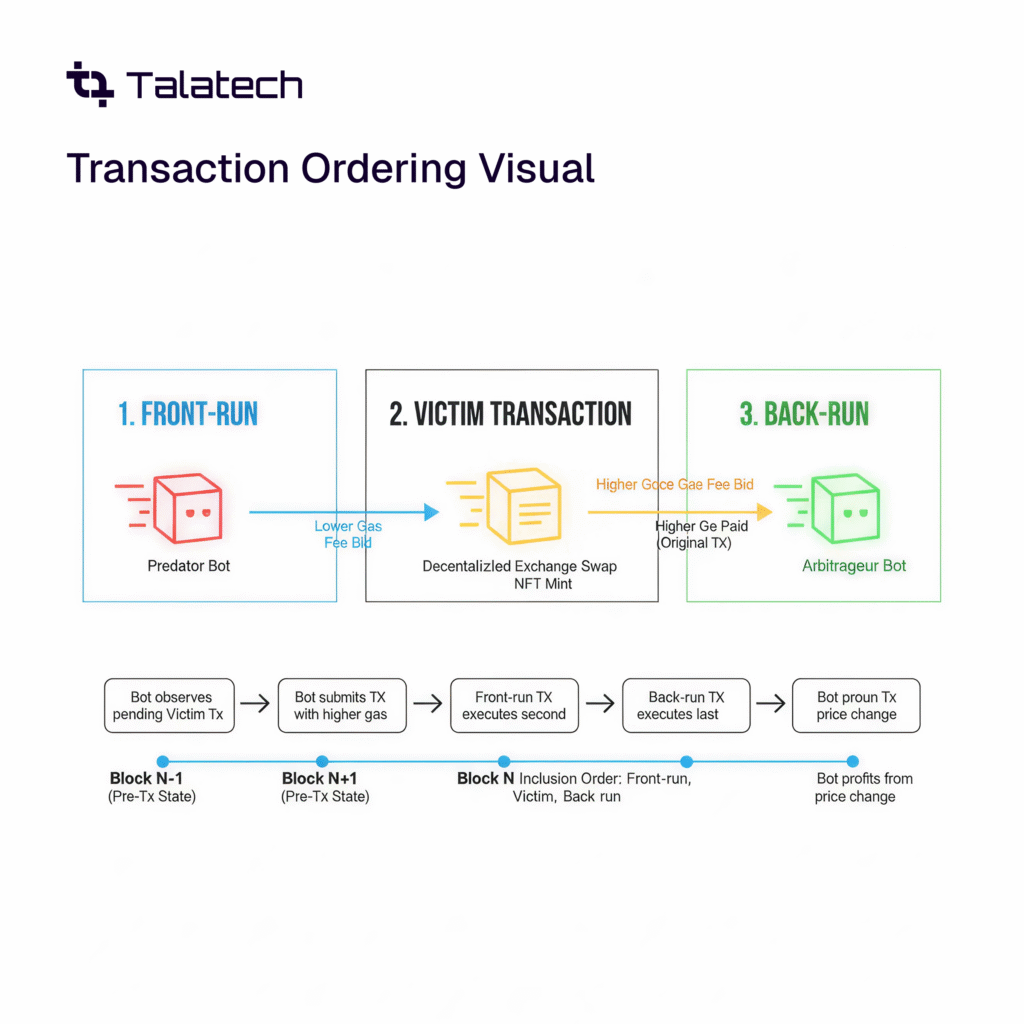
5. Front-Running Attacks
What it is:
Miners or bots exploit transaction order to gain profit, especially in DeFi systems with price updates or arbitrage opportunities.
How to Audit:
- Avoid unprotected public functions with price-sensitive logic.
- Use commit-reveal schemes or EIP-1559 gas prioritization.
- Test on simulated mainnet environments.
6. Denial of Service (DoS)
What it is:
Attackers force contracts into unresponsive states by exploiting gas limits or blocking functions.
How to Audit:
- Avoid unbounded loops
- Limit external dependencies.
- Test with gas stress simulations.
7. Insecure Randomness
What it is:
Using predictable sources like block.timestamp or blockhash allows attackers to manipulate supposedly random outcomes.
How to Audit:
- Use Chainlink VRF or similar oracle-based randomness.
- Avoid on-chain pseudo-random generation methods.
8. Timestamp Dependence
What it is:
Contracts that rely on timestamps for key logic (e.g., lotteries or unlocks) can be manipulated by miners.
How to Audit:
- Use block.number where feasible.
- Add time buffers to reduce sensitivity to miner manipulation.
9. Logic Errors and Uninitialized Variables
What it is:
Mistakes in initialization or condition logic can break tokenomics or governance mechanisms.
How to Audit:
- Review constructor and variable defaults.
- Conduct peer code reviews and automated static analysis.
- Ensure explicit initialization in all contracts.
10. Unprotected Self-Destruct and Upgradeability Risks
What it is:
Attackers may trigger a selfdestruct function or upgrade proxy contracts maliciously.
How to Audit:
- Restrict self-destruct permissions.
- Verify upgrade logic and proxy ownership.
- Use transparent upgradeable proxies (EIP-1967 standard).
Smart Contract Audit Checklist
Before deployment, use this smart contract audit checklist to ensure maximum security:
- Review access control modifiers (onlyOwner, onlyAdmin).
- Test for reentrancy and arithmetic overflow.
- Simulate gas-heavy scenarios to test resilience.
- Validate external calls and fallback functions.
- Use formal verification tools (e.g., MythX, Slither, Echidna).
- Perform independent third-party audits.
- Deploy on testnets and monitor with on-chain analytics.
- Implement continuous audit pipelines (CI/CD integration).
How to Audit Smart Contracts Efficiently
Modern audit workflows combine automated analysis, manual code review, and runtime testing. Security firms like CertiK, Trail of Bits, and OpenZeppelin recommend:
- Using static analysis tools for early detection.
- Maintaining audit logs and tracking changes in code versions.
- Reviewing dependencies, libraries, and third-party integrations thoroughly.
Conclusion
Smart contracts are immutable once deployed, making security audits indispensable. By understanding these top 10 smart contract vulnerabilities and following a robust smart contract audit checklist, teams can significantly reduce the risk of catastrophic exploits.
Security in Web3 is not a one-time taskit’s a culture of continuous improvement.